LOGIC.co.id – The dark web is often a subject shrouded in controversy and mystery. Known as a hidden and difficult-to-access part of the internet, it hosts various activities, both legal and illegal. Before deciding to explore, it’s essential to understand what the dark web is, how to access it, and the associated risks.
What is the Dark Web?
The dark web is a segment of the internet that is not indexed by search engines like Google or Bing. Access requires special software like Tor (The Onion Router). Unlike the deep web (unindexed content such as institutional databases or password-protected pages), the dark web is often associated with illegal activities such as drug trade, human trafficking, or hacking. However, it also serves legitimate purposes, such as providing secure communication for journalists and activists or discussing privacy rights.
How to Access the Dark Web Safely
1. Prepare Your Device and Basic Security
Before diving into the dark web, ensure your device is secure:
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic and hides your IP address, making it harder to trace your identity.
- Install Antivirus Software: The dark web is prone to malware; protecting your device is crucial.
2. Download and Install the Tor Browser
The Tor browser is the primary gateway to the dark web. Here’s how to set it up:
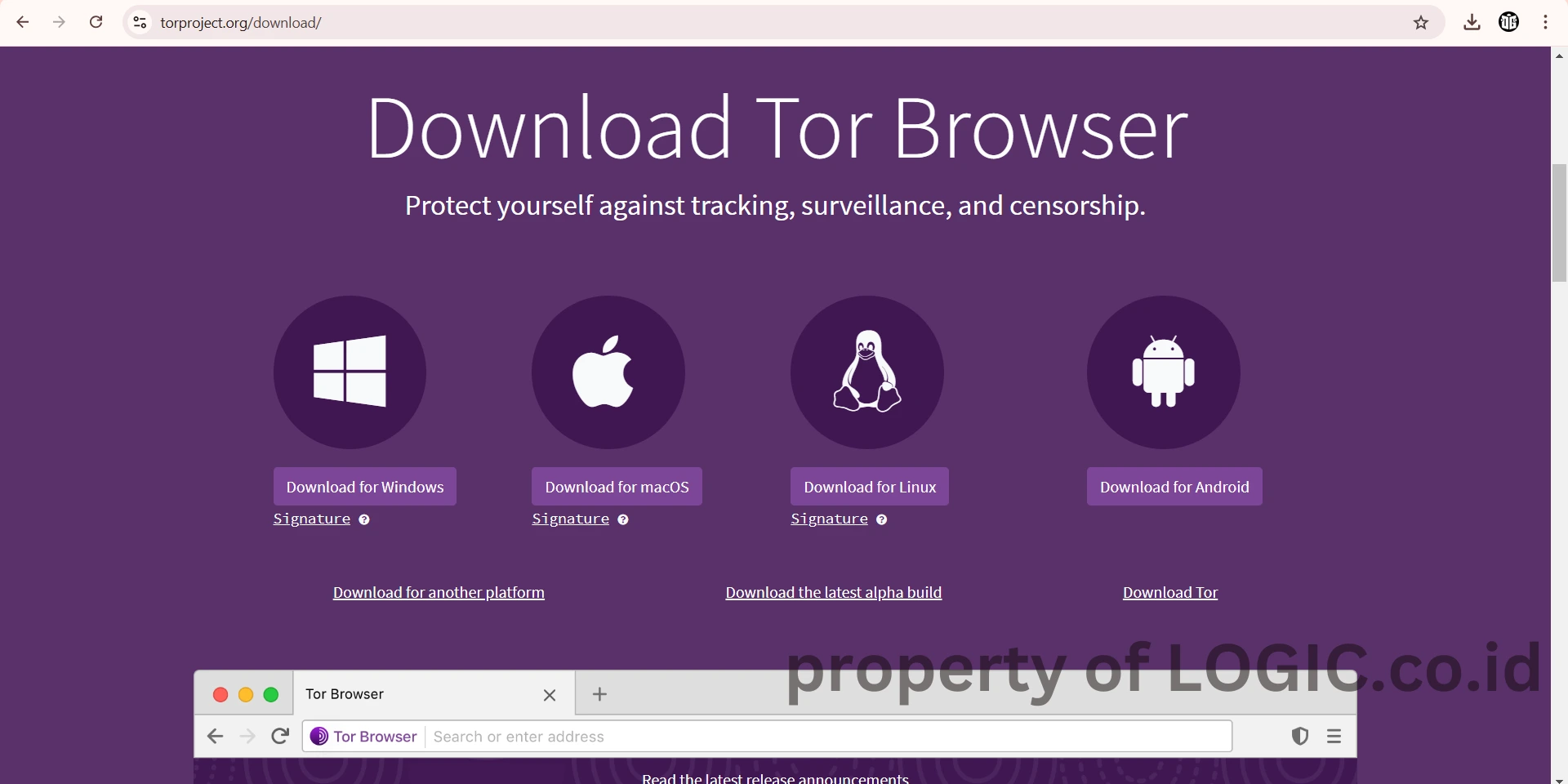
- Visit the official Tor Project website through the following link: Torproject
Once you are on the Tor Project homepage, click on “Download Tor Browser“

- Then scroll down.
Download the Tor Browser according to your device’s operating system (Windows, macOS, or Linux).
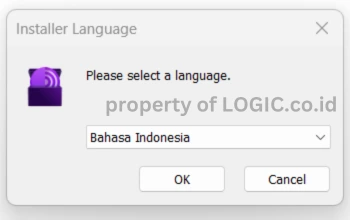
- Once downloaded, run the program, select your language, and then click “OK“
- Choose the location for the installation.
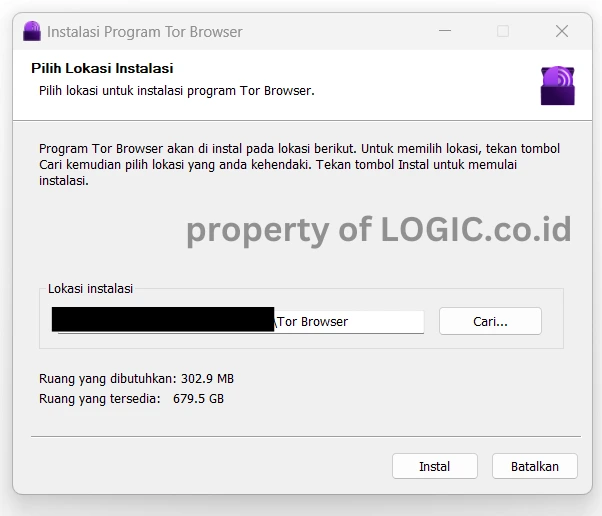
- Wait for the installation process to complete.

- The installation is complete; then click “Finish.”

- This is the main interface of the Tor Browser. Click “Connect” to access the dark web.

3. Access Websites with .onion Domains
Unlike regular websites, where we typically use domains like .co.id, .com, etc., sites on the dark web use a special domain with the .onion extension. Here are some ways to find these sites:
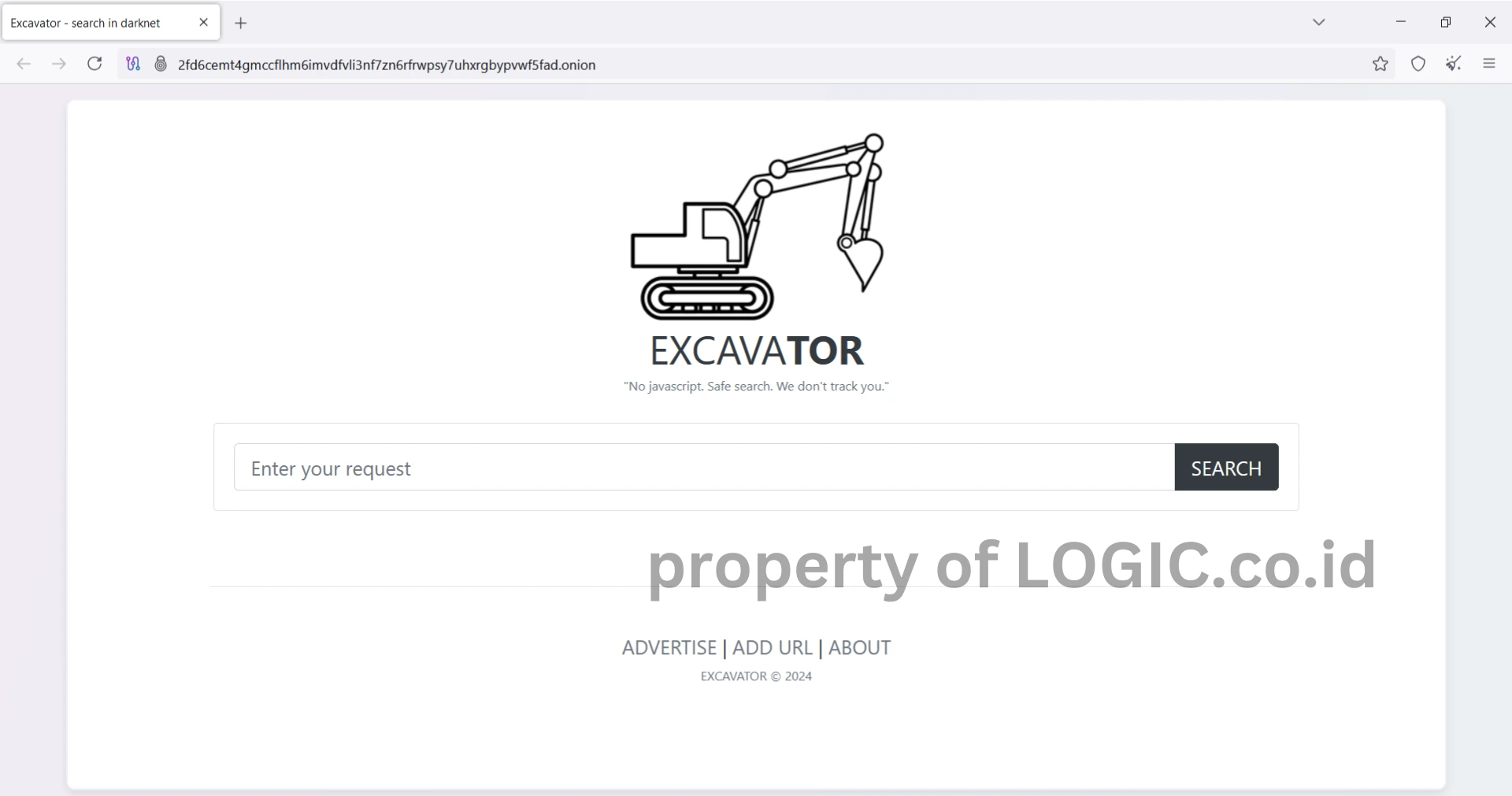
Dark Web Search Engines:
Here are some search engine links on the dark web that you can try:
2fd6cemt4gmccflhm6imvdfvli3nf7zn6rfrwpsy7uhxrgbypvwf5fad.onion
tor66sewebgixwhcqfnp5inzp5x5uohhdy3kvtnyfxc2e5mxiuh34iid.onion
3bbad7fauom4d6sgppalyqddsqbf5u5p56b5k5uk2zxsy3d6ey2jobad.onion
xmh57jrknzkhv6y3ls3ubitzfqnkrwxhopf5aygthi7d6rplyvk3noyd.onion
Official CIA Dark Web Site:
ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion

Dark Web Version of Wikipedia:
paavlaytlfsqyvkg3yqj7hflfg5jw2jdg2fgkza5ruf6lplwseeqtvyd.onion

What has been explained above is just a small part of what you can encounter on the dark web. There are numerous criminal activities, crimes, and other scams that we cannot elaborate on further. Therefore, be cautious if you decide to explore the dark web.
4. Avoid Logging In or Revealing Personal Information
Never use personal credentials when browsing the dark web. Stick to aliases and avoid sharing any identifiable information.
Risks to Be Aware Of
1. Malware Attacks
Many dark web sites are breeding grounds for malware. A single wrong click can infect your device with ransomware or trojans.
2. Scams
The dark web is notorious for scams. Many sites offer illegal goods or services but are designed to deceive users.
3. Surveillance by Authorities
Even with Tor, your activities may be monitored if you’re not cautious. Governments worldwide conduct operations to track dark web users.
4. Legal Consequences
Some activities on the dark web are illegal in many countries. Simply visiting certain sites or interacting with the wrong individuals can lead to legal repercussions.
Ethical and Legitimate Uses of the Dark Web
The dark web isn’t solely about illegal activities. Some legitimate reasons to access it include:
- Privacy: Protecting communication from censorship or government surveillance.
- Safety for Journalists and Activists: The dark web is often used by journalists and activists in countries with restricted freedom of speech.
- Research: Cybersecurity experts and criminal researchers often study threats on the dark web.
Tips to Stay Safe
- Avoid downloading suspicious files.
- Never make transactions using personal banking or credit card information.
- Use anonymous cryptocurrency wallets for payments, if necessary.
- Be cautious of phishing or fraudulent links.
Conclusion:
Accessing the dark web requires extra knowledge and caution. While there are potential benefits, the risks far outweigh them if you are not careful. Ensure you use the dark web ethically and for the right reasons.
The dark web is a double-edged sword; it can serve as a tool for protecting privacy or as a hub for dangerous activities. Use your discretion to explore this part of the internet safely.
Disclaimer: LOGIC.co.id does not support or endorse any illegal activities on the dark web. Due to the prevalence of fraud and criminal activities, we also advise against making any purchases using methods on the dark web.